Ok the screenshots don't really show everything I'd need to know to verify correct setup.
Windows machines typically have many IPv6 addresses and many of them are temporary, e.g. here one day and gone the next. So if possible, use DHCPv6 in the router to reserve and assign a specific address to the BI computer. Make sure the router's firewall rule is configured for that address. And make sure you are using that address to connect. Otherwise you can assign a static IPv6 address to the
Blue Iris PC as long as it is within your routed prefix but this is an advanced topic. Best to use DHCP(v6) if possible.
Then ensure these things:
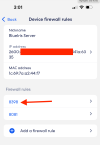
1) The router's firewall rule should ALLOW traffic on that port number (
8398) for TCP protocol. UDP is not necessary. And you only need to open one port, not two for Blue Iris's web server.
2) Blue Iris Settings > Webserver
- web server should be listening with HTTP and/or HTTPS on the same port number you opened in router's firewall. You can listen with both protocols on same port number.
Bind exclusively checkbox should NOT be checked
3) In Windows firewall advanced settings, add an inbound rule allowing TCP traffic on port
8398 or whatever port you end up using. Allow it for all network types (public/private/domain). This is normally redundant with the automatically created firewall rule for Blueiris.exe, but has the benefit of still working after Windows has mistakenly changed your network type to public.
Then one way of testing connectivity is to use a web browser, build the URL like this:
http://[2600....41a:6335]:8398/
Fill in the real IPv6 address. Actual square brackets go around the IPv6 address; don't take those out.
I've never used IPv6 in the mobile app so I don't know if it has any quirks there.